Amazon Data Breach incident and Solutions to Prevent Information Leakage
- Home
- Support
- Tips SecureSilo
- Amazon Data Breach incident and Solutions to Prevent Information Leakage
Summary
With the popularity of Internet applications and people's dependence on the Internet, Internet security issues have become increasingly prominent. In recent years, large and small leaks have occurred frequently, not only personal information has been leaked, but some large companies and famous websites have also leaked important data.
I. Amazon information leakage incident
Last year, the renowned website Amazon experienced a security breach, resulting in the leakage of some consumers’ personal information. This incident escalated in January of this year when several Amazon employees were bribed and colluded with sellers to trade information, leading to a significant leak of buyer data. This incident underscores that even trustworthy websites can experience data breaches, emphasizing the importance of maintaining confidentiality. So, how can we better protect our information? The two software recommendations below can assist us.

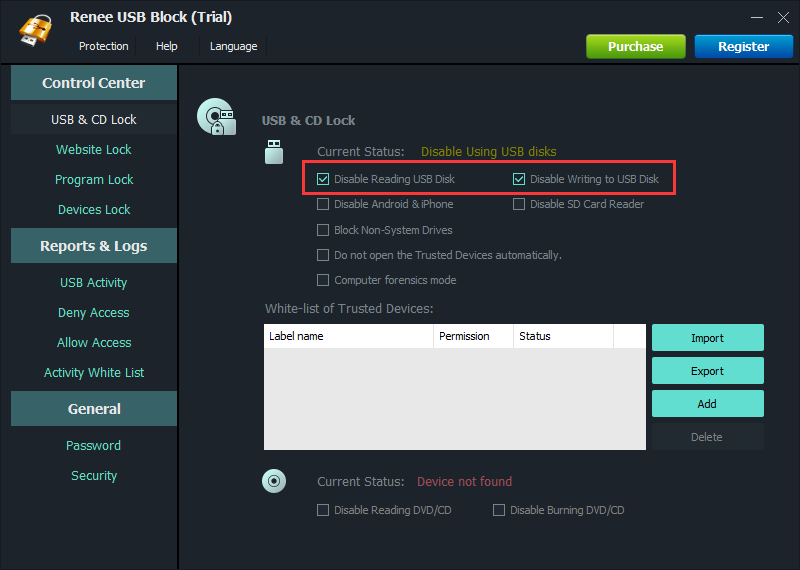
II. Renee USB Block
With the rise of portable storage devices and removable media, data breaches have become a serious threat to organizations and individuals. Of course, we try to protect the data on our computers. But how do we ensure that there are no threats to external devices and prevent unauthorized external devices from accessing the computer?

Easily use Simple operations fit green hands and professionals.
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
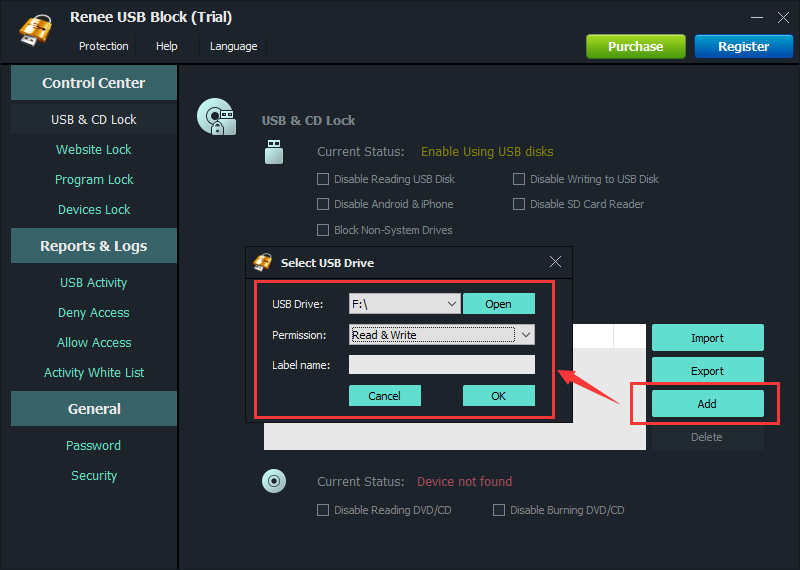
Control and lock Users can lock devices, websites, applications and USB ports.
Monitor and logs Users can select the target directory to monitor and generate the history.
Self protection Lock itself if users enter the wrong passwords 5 times. Notification will be sent once wrong password entered over 5 times and password change. Password is also necessary when uninstalling.
Easily use Simple operations fit green hands and professionals.
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
Monitor and logs Monitor target directory and generate the history.
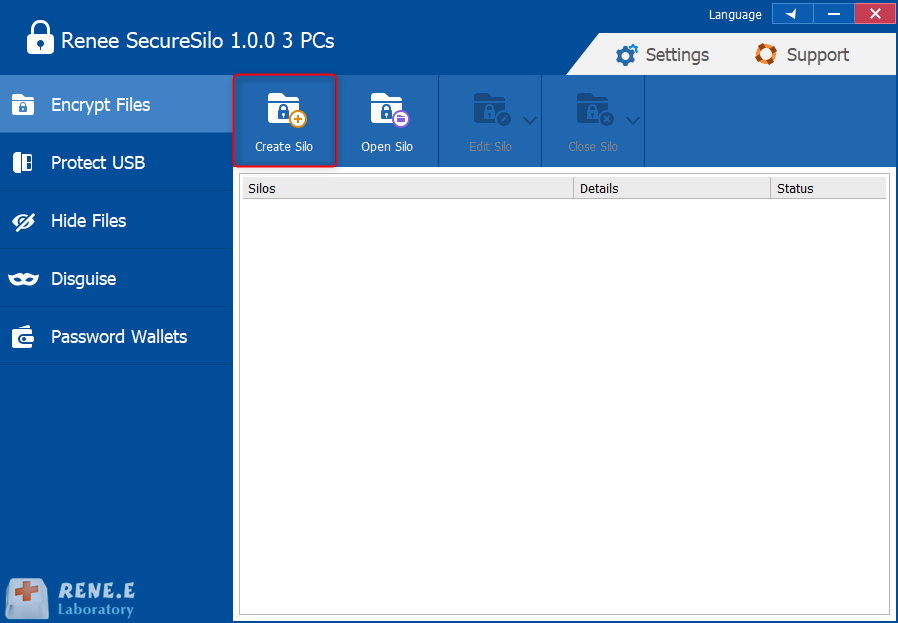
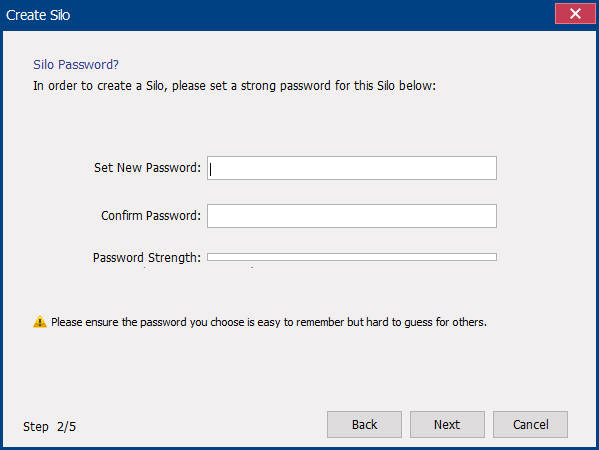
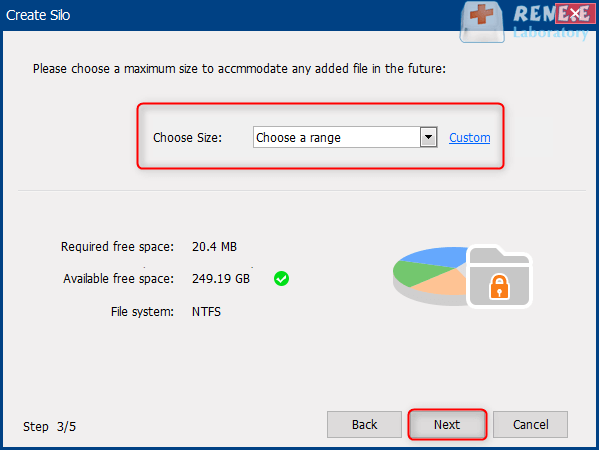
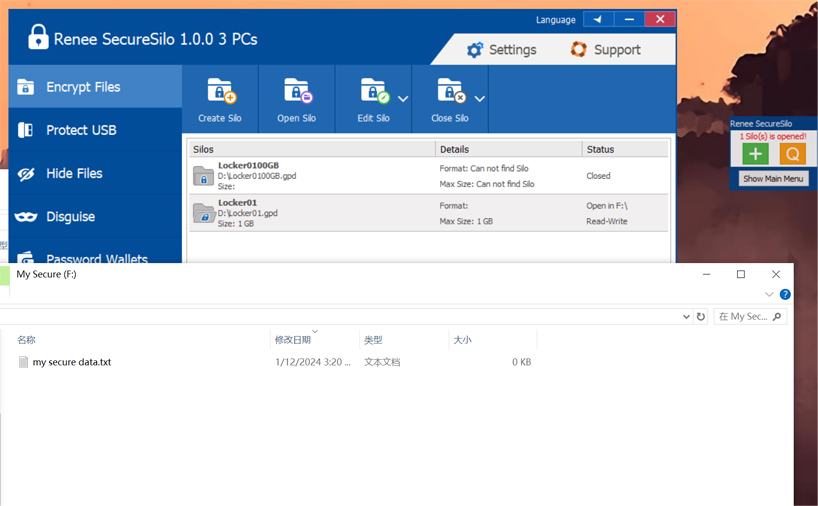
III. Renee SecureSilo

Encrypt files in seconds Encrypt files with virtual encrypted disk and whole process can be finished in 1 second.
User friendly Concise interface helps users master the software in short time.
High Security AES256 encryption algorithm helps Renee Seecure Silo encrypt files confidentially.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
Overall Data Protection Solution Protect data in USB disk/hide/disguise files/ Password wallet.
Easy to use Few clicks for whole encryption process.
User friendly Concise interface helps users master the software in short time.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
IV. Summary
Relate Links :
Inspiration from the Huawei Data Leak Incident
11-03-2024
Amanda J. Brook : With the relentless evolution of the Internet, we've unlocked immense conveniences that have transformed our daily existence. However,...
Internet Risks and Rewards: A Look at Data Breach Compensation
08-02-2024
Amanda J. Brook : In the Internet age, easy access to information comes with the risk of personal data breaches. Such exposure...
Small Business File Encryption: Keep Your Data Safe
01-02-2024
Amanda J. Brook : Protect your enterprise's core data by encrypting important files and folders. This method is the most direct way...
17-12-2020
Amanda J. Brook : We pay attention to privacy protection at any time. Especially in the network era, the data in a...




