Powerful Tools to Prevent Data Breach
- Home
- Support
- Tips Renee USB Block
- Powerful Tools to Prevent Data Breach
Summary
Now, many companies keep the important files in computers. But this is not an entirely safe way. Data disclosure will occur if we simply save them in the computer. In this essay, we will mainly talk about why files will be stolen and introduces the powerful tools to prevent data breach.
Leaks by employees – Some employees may send the important files by web mail or print them out. That can cause data leaks.
Take the unlocked files outside – As we all know, we usually meet with clients, with the important files taken. But it is a potential risk of data breach. If the files saved in the USB flash drive are not locked, they will be leaked once the USB is inserted into the virus-affected computer.


Easily use Simple operations fit green hands and professionals.
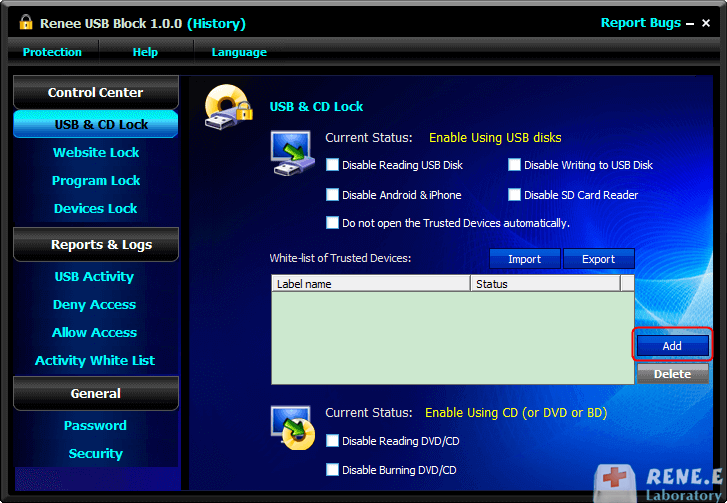
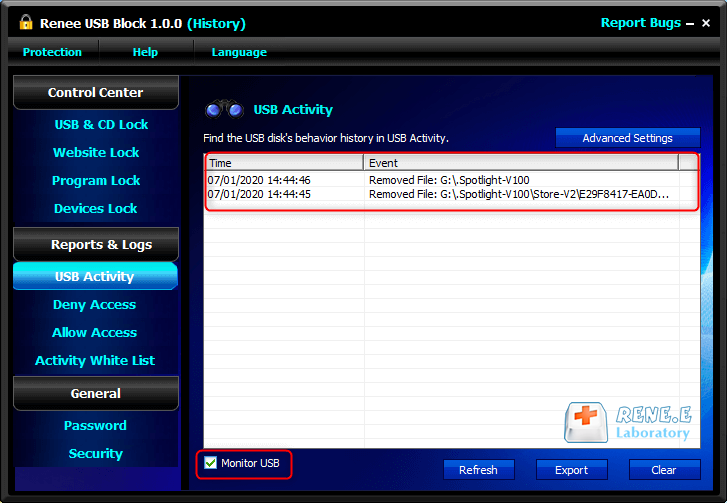
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
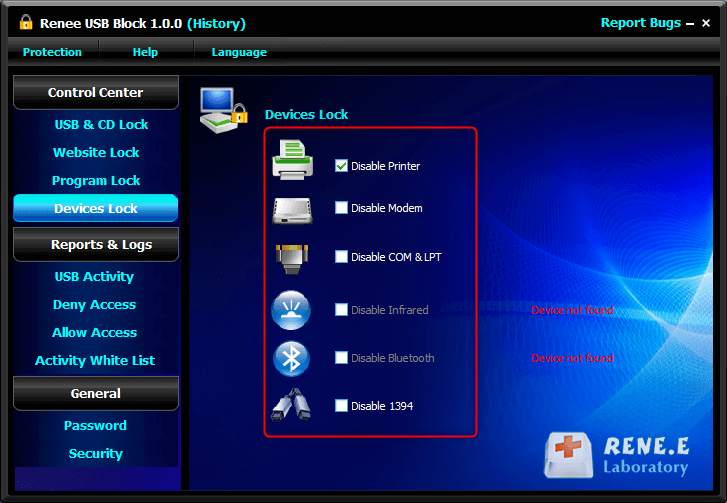
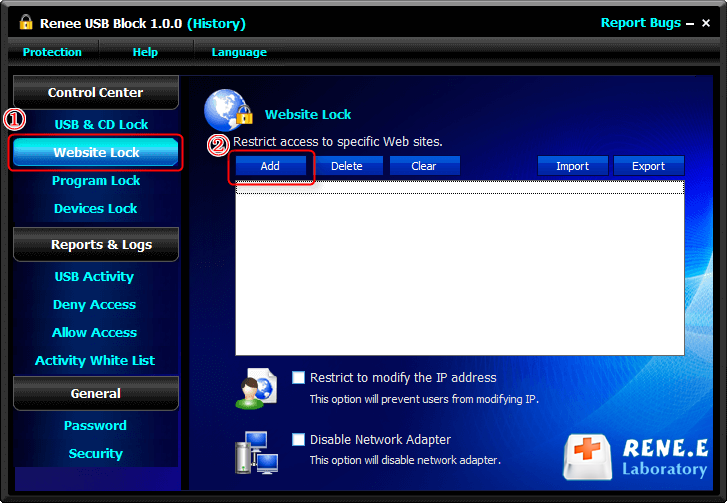
Control and lock Users can lock devices, websites, applications and USB ports.
Monitor and logs Users can select the target directory to monitor and generate the history.
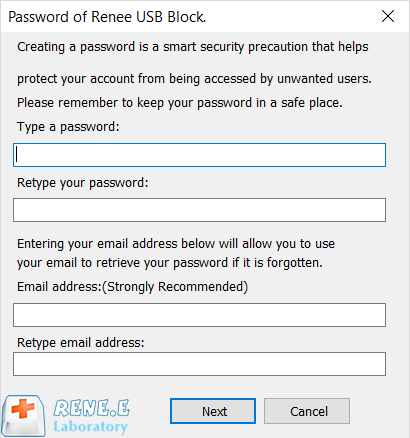
Self protection Lock itself if users enter the wrong passwords 5 times. Notification will be sent once wrong password entered over 5 times and password change. Password is also necessary when uninstalling.
Easily use Simple operations fit green hands and professionals.
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
Monitor and logs Monitor target directory and generate the history.
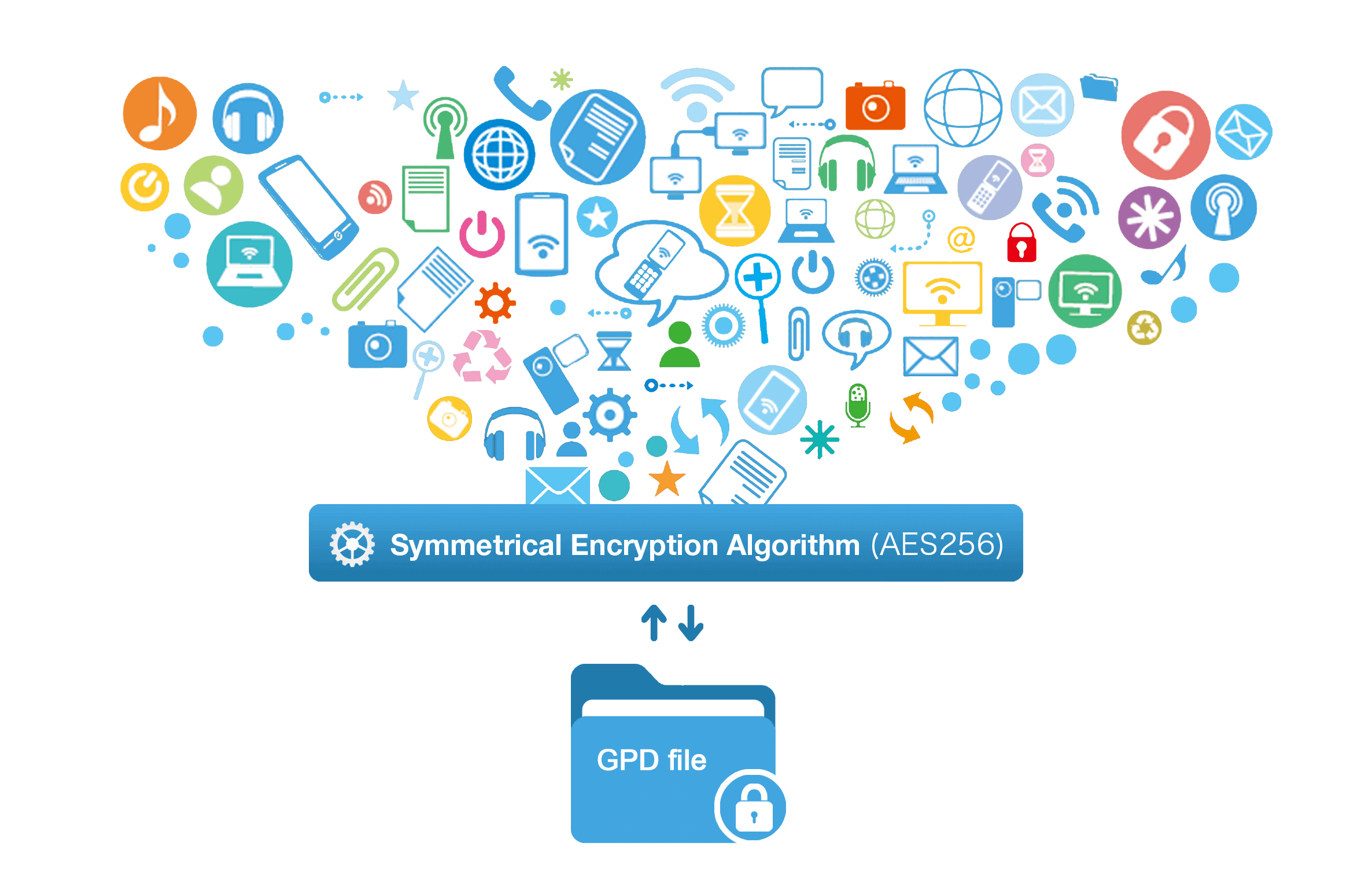

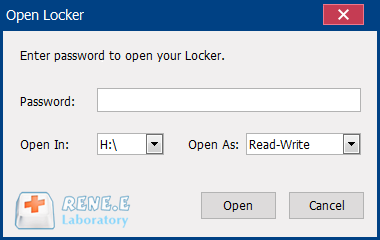
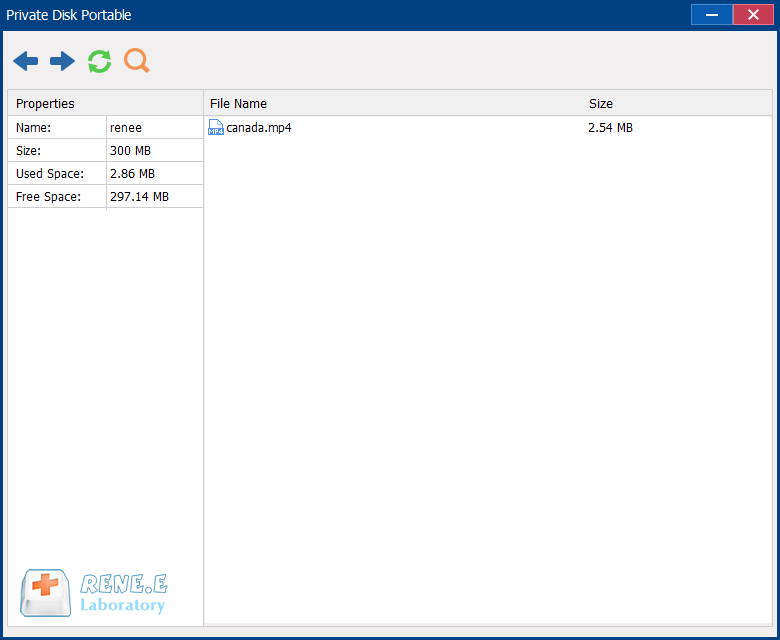
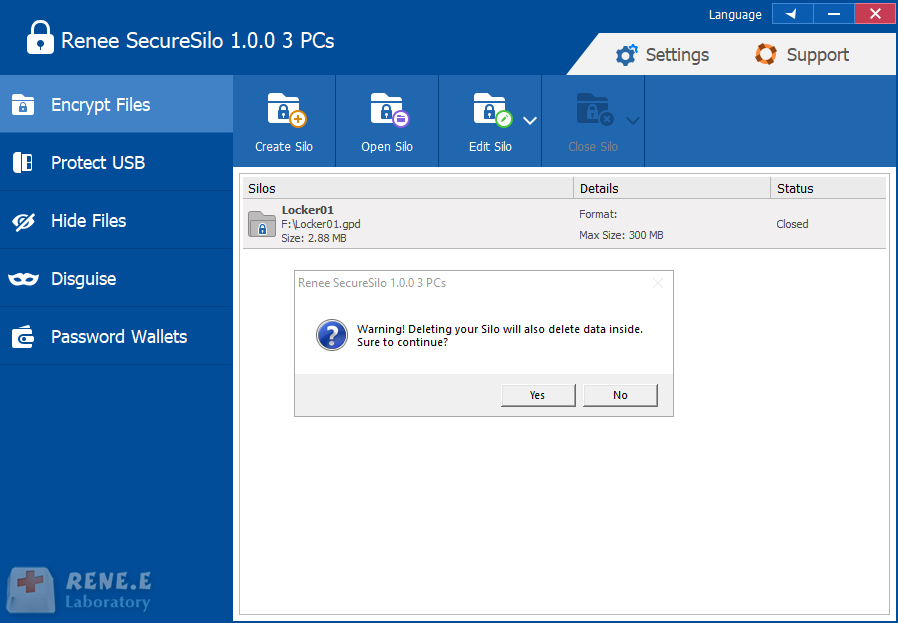
Encrypt files in seconds Encrypt files with virtual encrypted disk and whole process can be finished in 1 second.
User friendly Concise interface helps users master the software in short time.
High Security AES256 encryption algorithm helps Renee Seecure Silo encrypt files confidentially.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
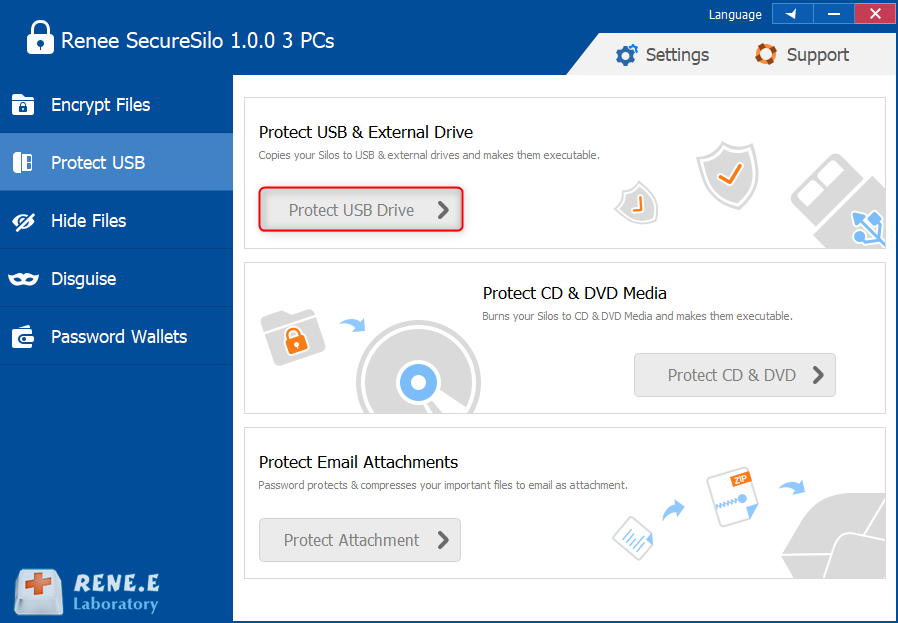
Overall Data Protection Solution Protect data in USB disk/hide/disguise files/ Password wallet.
Easy to use Few clicks for whole encryption process.
User friendly Concise interface helps users master the software in short time.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
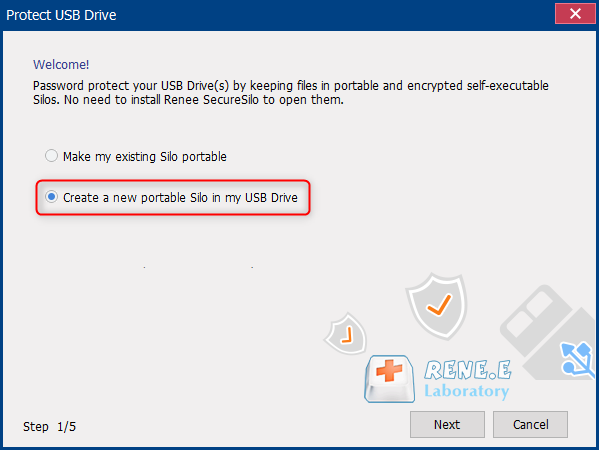
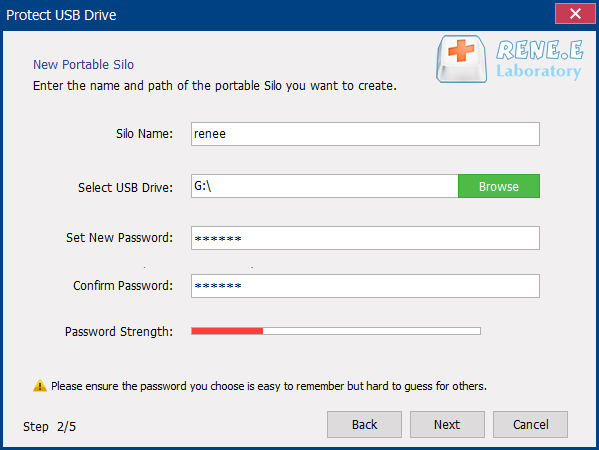
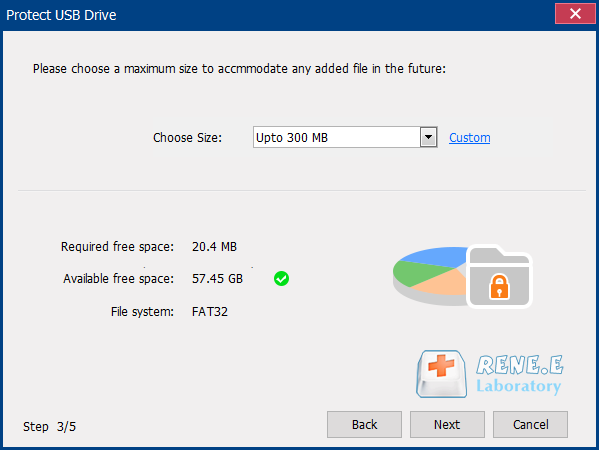
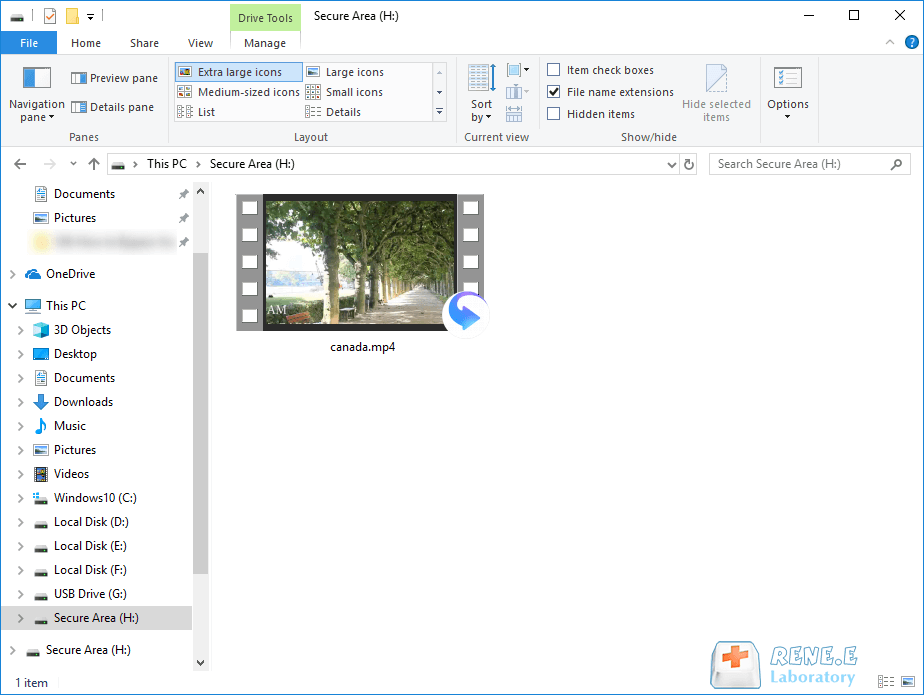
Relate Links :
How to Realize Computer Remote Control?
01-07-2020
Ashley S. Miller : Sometimes, we control a computer with another computer. Yet, many people don’t know how to realize computer remote...
13-01-2021
Amanda J. Brook : No matter you are using a Windows or Mac OS computer, you are certainly saving files to the...




