Set Password for A File: Top Tips for Ultimate File Encryption Security
- Home
- Support
- Tips Renee File Protector
- Set Password for A File: Top Tips for Ultimate File Encryption Security
Summary
Learn how to set password for a file with robust encryption techniques and defend against potential breaches with our guide on secure password setting.
- Choose your own encryption method and related precautions
- ◆ Encryption method suitable for transmission
- ◆ Encryption method suitable for modification
- ◆ Precautions
- Convenient Transfer – How to set a secure access password for important files?
- ◆ Method 1: (Format Private) Encrypt with Renee File Protector
- ◆ Method 2: Use Renee SecureSilo to compress and encrypt
- ◆ Method 3: Use WinZip to compress encrypted files
- ◆ Method 4: Use WinRAR to compress encrypted files
- ◆ Due to the open format, compressed files such as Zip and RAR are easy to be cracked
Why set access passwords for important files?

Choose your own encryption method and related precautions
Encryption method suitable for transmission
 advantage advantage |  shortcoming shortcoming | |
|---|---|---|
| compression encryption | ● Minified files for easy transfer over the network ● Widely supported, most software supports reading the content of compressed files | ● It is not conducive to modification, and it takes a long time to modify a single file. ● For compressed and encrypted formats such as zip and rar, there are many cracking software on the Internet |
Encryption method suitable for modification
- Hardware encryption refers to the encryption capabilities integrated directly within a storage device, which automatically encrypts and stores all incoming data. Access to this data requires the provision of authorized token information. Such security measures are most commonly implemented by large corporations and can become expensive due to the requirement for a comprehensive range of compatible peripherals.
- Full-disk encryption employs software solutions such as BitLocker (which is not supported by all versions of Windows Home) or TrueEncrypt to secure entire disk partitions at the sector level. To access the encrypted data, users must enter the correct password.
- Virtual disk encryption utilizes software programs like Renee SecureSilo to generate a secure, encrypted virtual disk file that can be mounted to a drive letter. Much like a USB flash drive, it can be accessed as needed and secured when not in use. Utilizing virtual loading technology, this method is particularly covert, allowing virtual disk files to be camouflaged as different file types for enhanced secrecy.
 advantage advantage |  shortcoming shortcoming | |
|---|---|---|
| hardware encryption | ● Fastest encryption and decryption ● Very high security | ● Expensive ● Need a lot of supporting facilities |
| full disk encryption | ● Fast encryption and decryption ● The initial encryption process is long ● Low price, high performance-price ratio | ● Moderate privacy ● Requires a specific version of Windows to use (not all Home versions are supported) ● Average level of security |
| virtual disk encryption | ● Fast encryption and decryption ● You can customize the size of the virtual disk at will ● Can be loaded and closed at any time, with strong privacy ● very cost-effective | ● Average level of security |
Precautions
- Use a memorable password when encrypting files to avoid forgetting it.
- While no encryption is foolproof, opt for professional encryption software with robust security to deter cracking.
- Encrypted files and folders can still be deleted, so back up vital data before encryption.
Convenient Transfer - How to set a secure access password for important files?
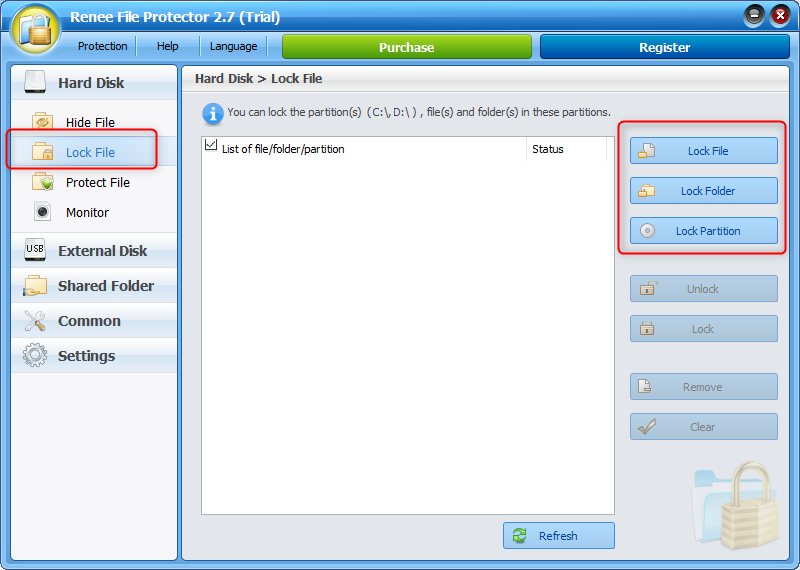
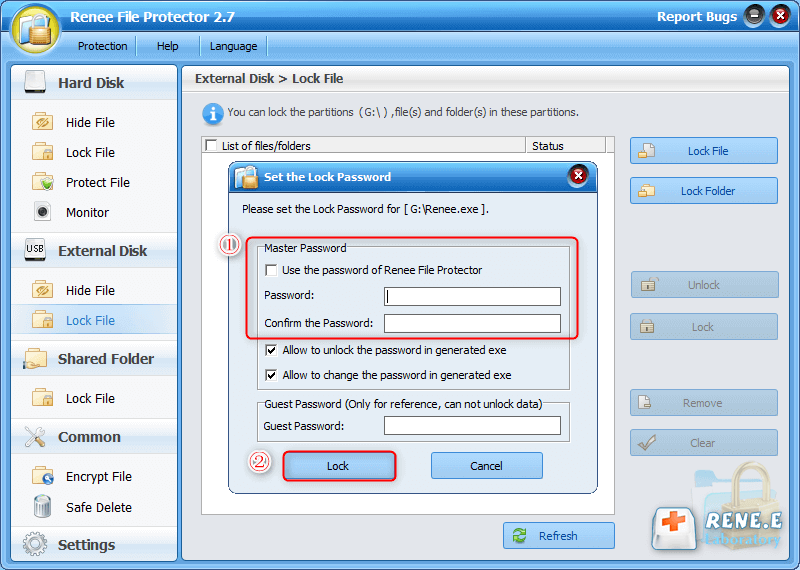
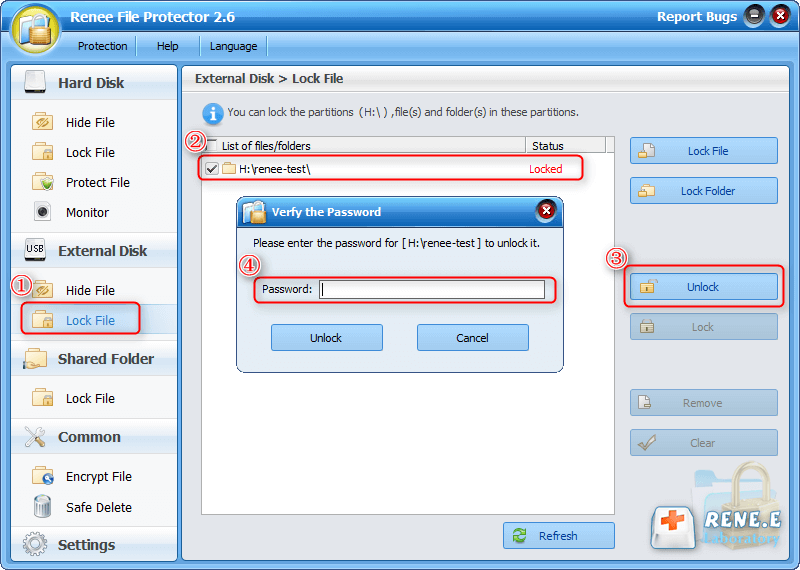
Method 1: (Format Private) Encrypt with Renee File Protector

Easy to use Few clicks for whole folder encryption process.
Overall protection Users can hide, lock or get other protection to files in local disk or USB disk.
High Security Classified encryption method prevents data from leakage.
Compression transfer Support to compress and encrypt any files to secure the file transfer security.
Advanced self protection Provide self
Easy to use Few clicks for whole folder encryption process.
Overall protection Users can hide, lock or get other protection to files in local disk or USB disk.
High Security Classified encryption method prevents data from leakage.
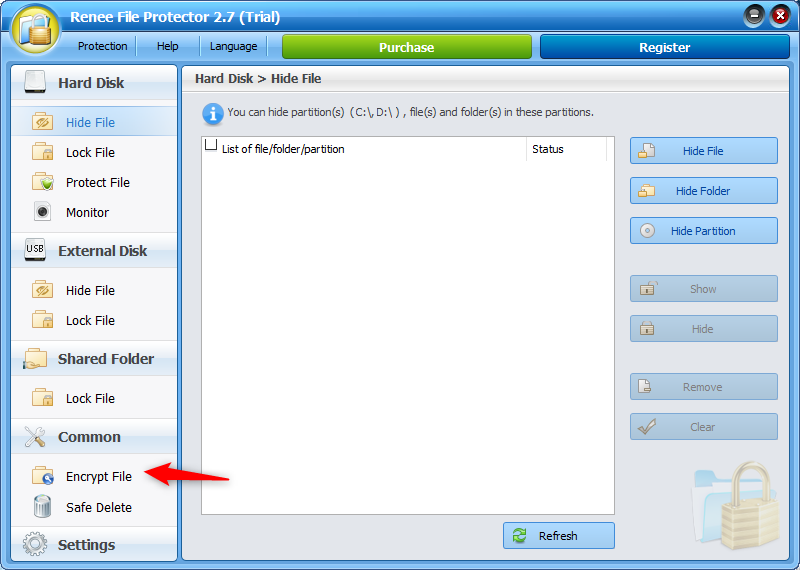
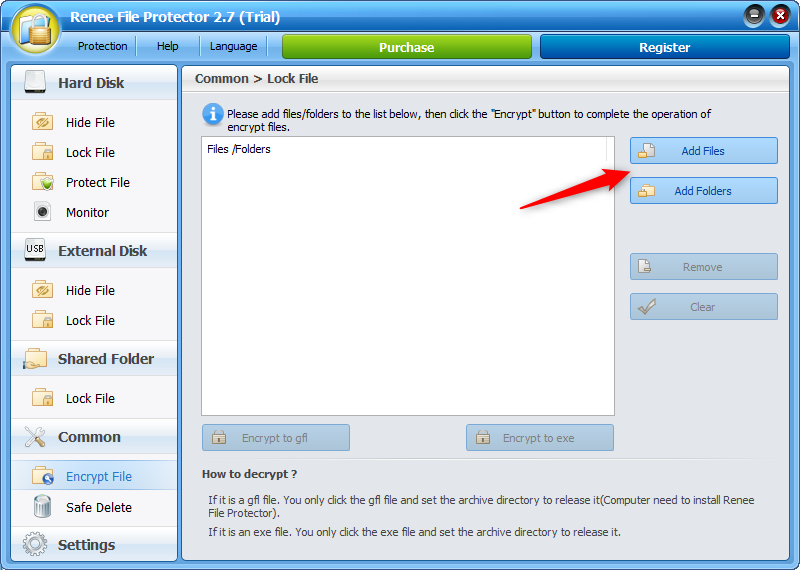
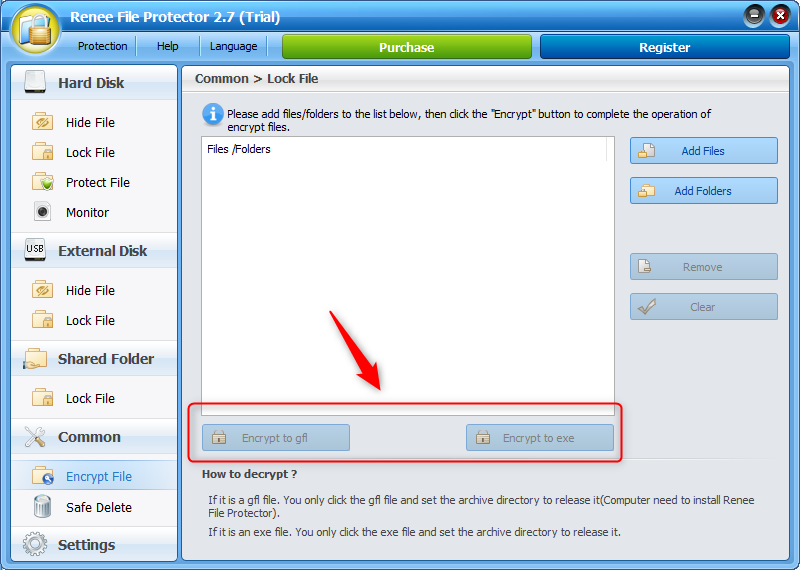
GFL vs. EXE Encryption Formats:
GFL: Encryption ties the file to the original computer with Renee File Protector installed, making it ideal for secure data transfer between specific, software-equipped machines.
EXE: Allows password-protected decryption without needing Renee File Protector, offering greater flexibility for password holders to safely transfer and decrypt files. Recommended for general data transfer.
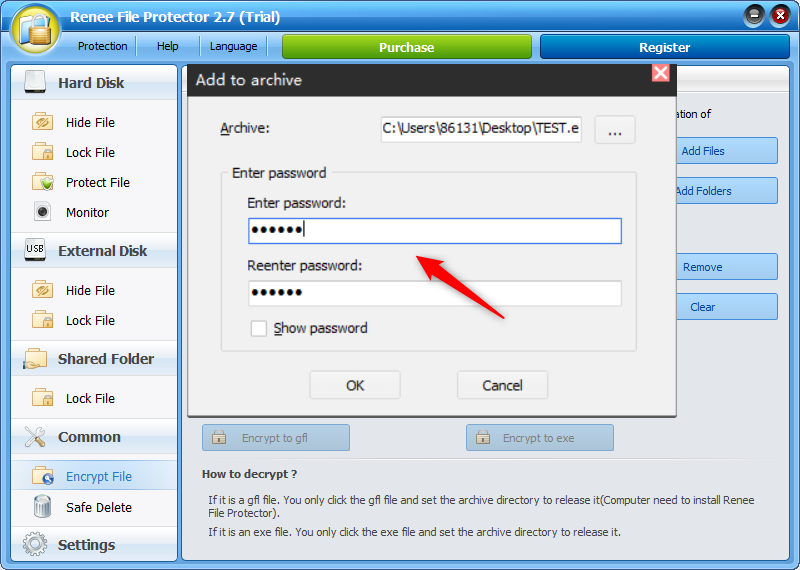
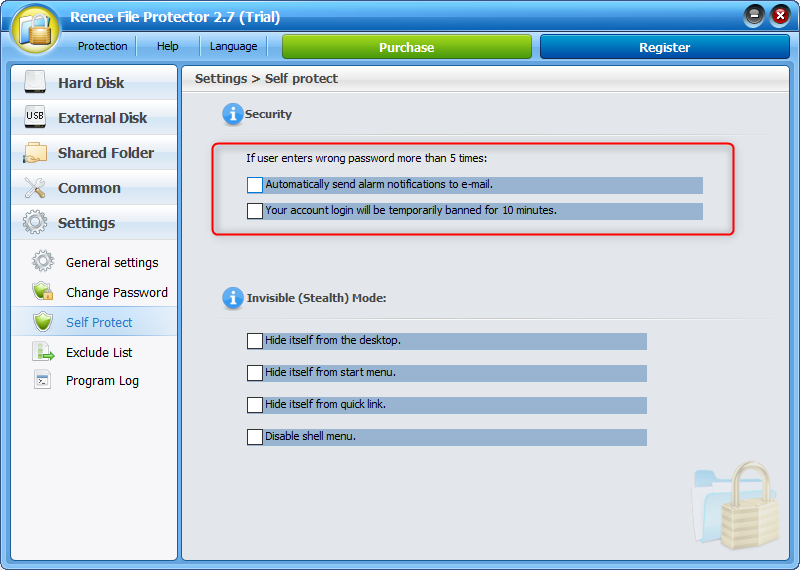
● The software is powerful and supports multiple encryption and locking methods. And the software can carry out self-protection settings to prevent brute force cracking. As long as the password is entered incorrectly for 5 consecutive times, the software will automatically send an email to the mailbox to notify that the crack has occurred. And it can be set to prohibit the operation of entering password access within 10 minutes.
Method 2: Use Renee SecureSilo to compress and encrypt

Encrypt files in seconds Encrypt files with virtual encrypted disk and whole process can be finished in 1 second.
User friendly Concise interface helps users master the software in short time.
High Security AES256 encryption algorithm helps Renee Seecure Silo encrypt files confidentially.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
Overall Data Protection Solution Protect data in USB disk/hide/disguise files/ Password wallet.
Easy to use Few clicks for whole encryption process.
User friendly Concise interface helps users master the software in short time.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
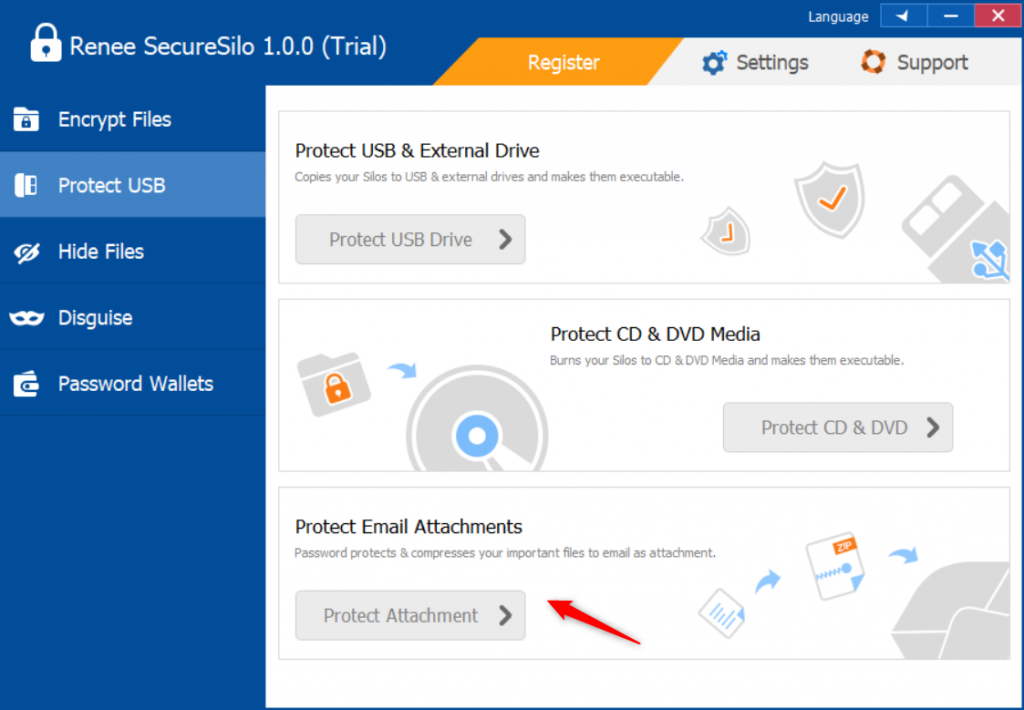
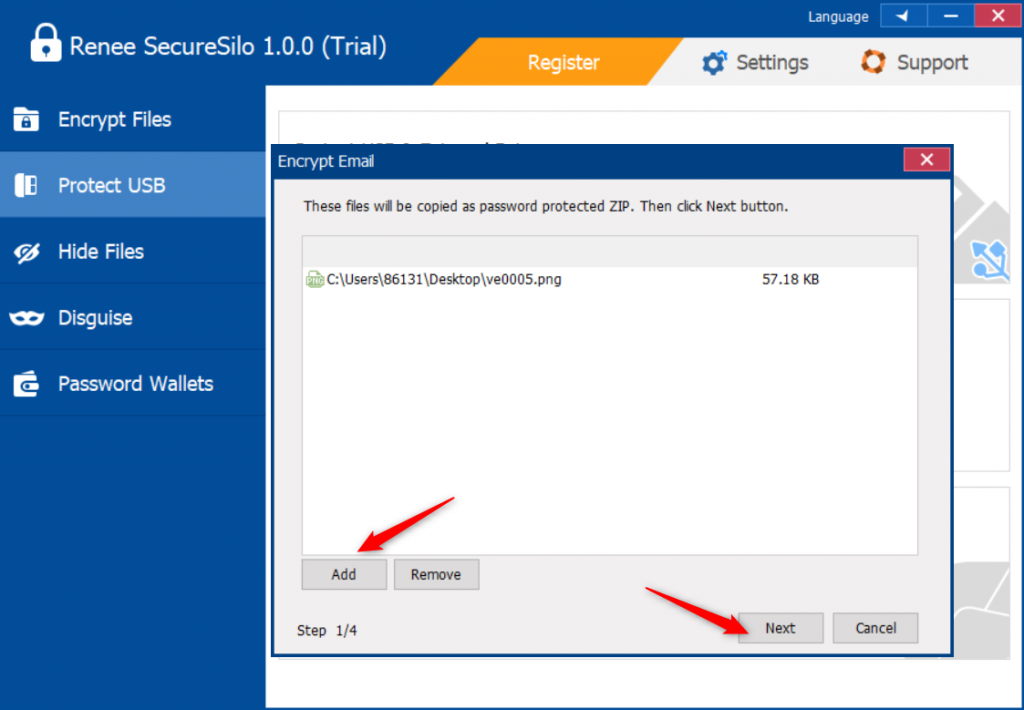
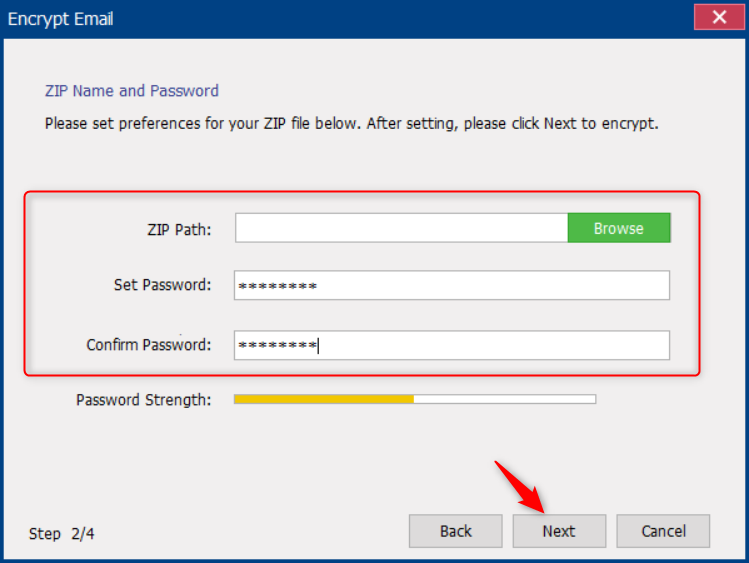
● The software adopts advanced AES256 encryption technology, and there is no universal cracking program available on the market, which is difficult to crack. The software is powerful and supports multiple encryption methods.
Method 3: Use WinZip to compress encrypted files
● Since the initial design of various compression software is mainly for the convenience of storage and transmission, it will be very time-consuming to modify encrypted files. Moreover, there are a large number of cracking software for compressed files on the Internet, and their security cannot be guaranteed. Even if they are encrypted, they can be cracked through simple steps.
Method 4: Use WinRAR to compress encrypted files
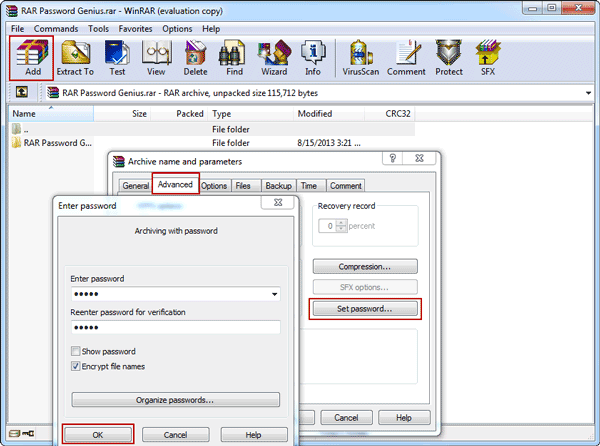
● Since the initial design of various compression software is mainly for the convenience of storage and transmission, it will be very time-consuming to modify encrypted files. Moreover, there are a large number of cracking software for compressed files on the Internet, and their security cannot be guaranteed. Even if they are encrypted, they can be cracked through simple steps.
Due to the open format, compressed files such as Zip and RAR are easy to be cracked
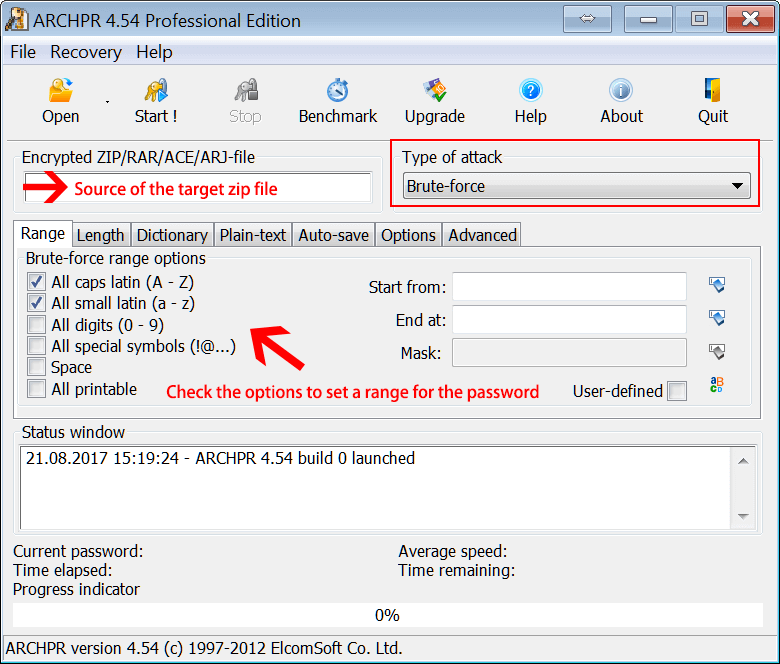
IV Modification - How to set a secure access password for files that are frequently modified?
Method 1: (Virtual Encrypted Disk) Use Renee SecureSilo to encrypt files

Encrypt files in seconds Encrypt files with virtual encrypted disk and whole process can be finished in 1 second.
User friendly Concise interface helps users master the software in short time.
High Security AES256 encryption algorithm helps Renee Seecure Silo encrypt files confidentially.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
Overall Data Protection Solution Protect data in USB disk/hide/disguise files/ Password wallet.
Easy to use Few clicks for whole encryption process.
User friendly Concise interface helps users master the software in short time.
Encrypt any Data Support to encrypt images, videos, Office documents and software.
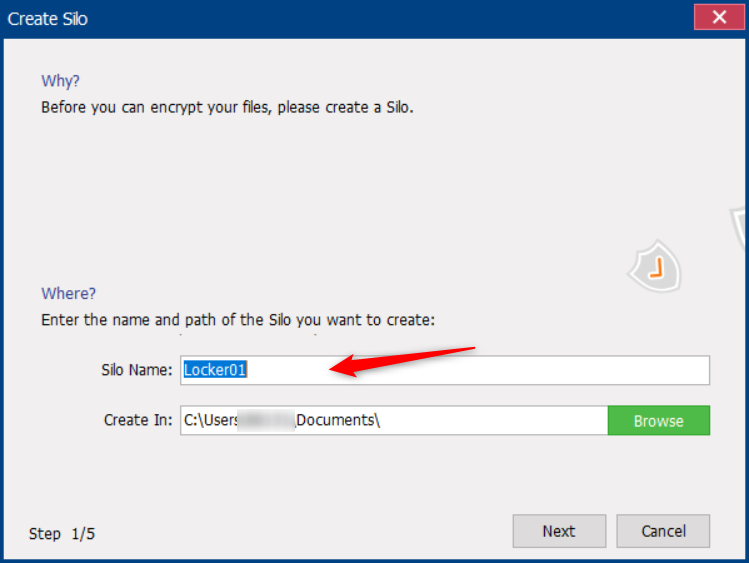
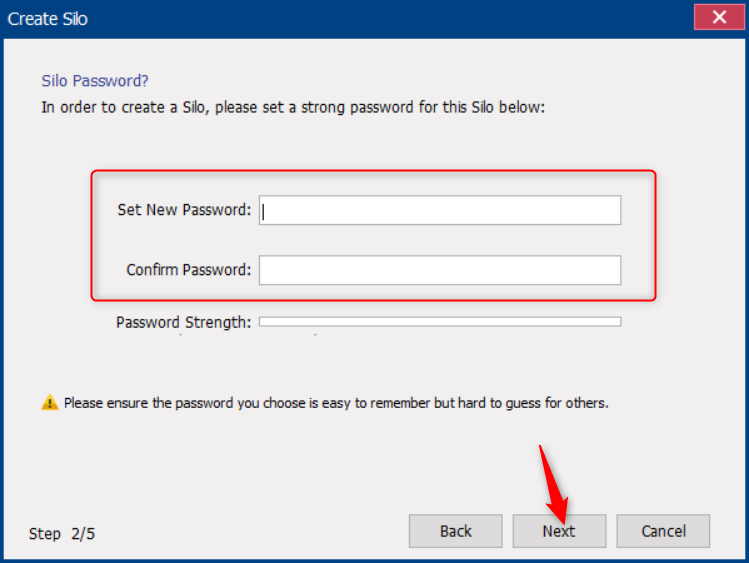
● The software adopts AES256 encryption algorithm, the key strength is high, and it is not easy to be cracked. Moreover, this software can encrypt files in large quantities, which is easy to modify and does not take time. It is very suitable for the storage and modification of encrypted files.
Method 2: (full disk encryption) use Bitlocker for file encryption
All Windows Home editions do not support BitLocker.
- Windows Vista and Windows 7 Ultimate and Enterprise
- Windows 8 and 8.1 Professional and Enterprise
- Windows 10 Professional, Enterprise and Education editions
- Windows Server 2008 and later systems
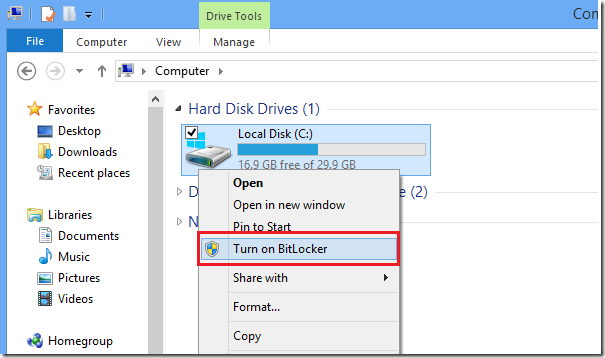
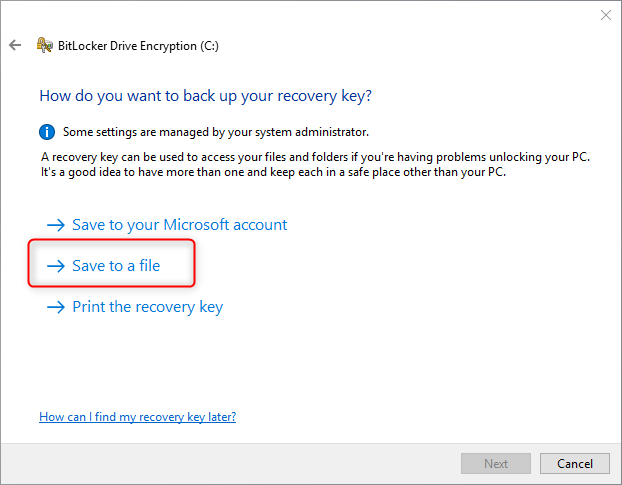
● Due to its limited functions, Bitlocker cannot encrypt a file or folder individually, but can only encrypt the entire disk where the file is located, indirectly achieving the purpose of file encryption. When the user needs to open other files in the disk, he needs to enter the password every time, which is extremely cumbersome. And it doesn't work with Home Edition.
How to further protect important information to prevent leakage?

Easily use Simple operations fit green hands and professionals.
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
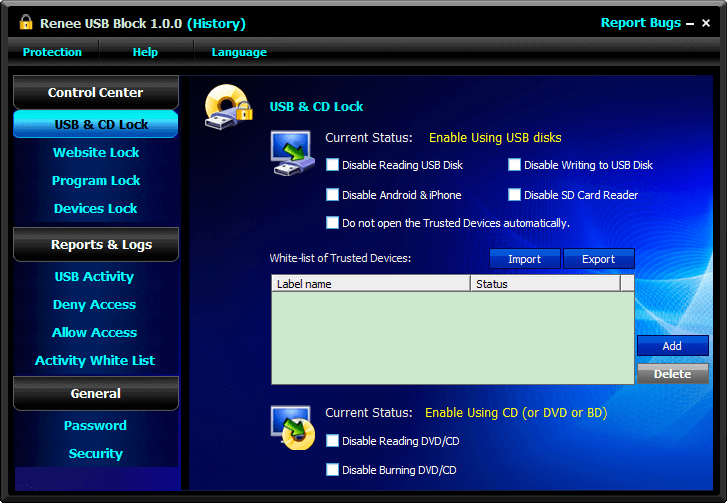
Control and lock Users can lock devices, websites, applications and USB ports.
Monitor and logs Users can select the target directory to monitor and generate the history.
Self protection Lock itself if users enter the wrong passwords 5 times. Notification will be sent once wrong password entered over 5 times and password change. Password is also necessary when uninstalling.
Easily use Simple operations fit green hands and professionals.
Prevent from privacy leak Unauthorized external devices cannot run or obtain any information in PC.
Monitor and logs Monitor target directory and generate the history.
How can VI prevent encrypted important files from being cracked?
- Passwords must be at least 8 characters long.
- Incorporate a mix of upper/lowercase letters, numbers, and symbols to enhance complexity.
- Avoid using identical passwords for multiple encrypted files.
- Refrain from using personal details like your name’s pinyin or birth date as a password.
- Do not use personal information that can be easily found, such as license plate or phone numbers, and home addresses.

Easy to use Few clicks for whole folder encryption process.
Overall protection Users can hide, lock or get other protection to files in local disk or USB disk.
High Security Classified encryption method prevents data from leakage.
Compression transfer Support to compress and encrypt any files to secure the file transfer security.
Advanced self protection Provide self
Easy to use Few clicks for whole folder encryption process.
Overall protection Users can hide, lock or get other protection to files in local disk or USB disk.
High Security Classified encryption method prevents data from leakage.
Relate Links :
How to Unlock Protected PDF Files?
18-12-2020
Amanda J. Brook : In our daily life, some people forget the password of the locked files. How can we unlock the...
How to Password Protect a PDF File without Acrobat?
31-12-2020
Ashley S. Miller : Sometimes, we don’t want to share or print the PDF files. How can we keep them well? In...
How to Password Protect Excel Files?
05-08-2020
Ashley S. Miller : Excel files are always around our office work. Many people prefer to encrypt the Excel files for privacy...
How to Create Password-Protected Zip Files Better?
14-07-2020
Amanda J. Brook : If some people want to encrypt a file, they can zip it and add a password to the...




